Most people who are not involved with cybersecurity in their professional careers typically refer to all the malware as “computer viruses”. However, not all malware is the same. In fact, there are several distinct types of malware. Each type has its own characteristics, operating procedures, goals, delivery methods, etc. In this article, we will take a look at the 9 most common types of computer malware.

Table of Contents
What is malware?
Malware is short for malicious software. It refers to any computer program that was created with the goal of causing harm, getting unauthorized access to information, etc.
Types of malware
Computer viruses
This is the most common kind of malware and one everyone has heard about. Viruses are commonly found in the following file types: .html, .doc/docx, .zip, .exe, .xls/.xlsx. This type of malware quickly replicates and spreads to numerous devices through email, USB devices, wireless networks, instant messaging applications, etc.
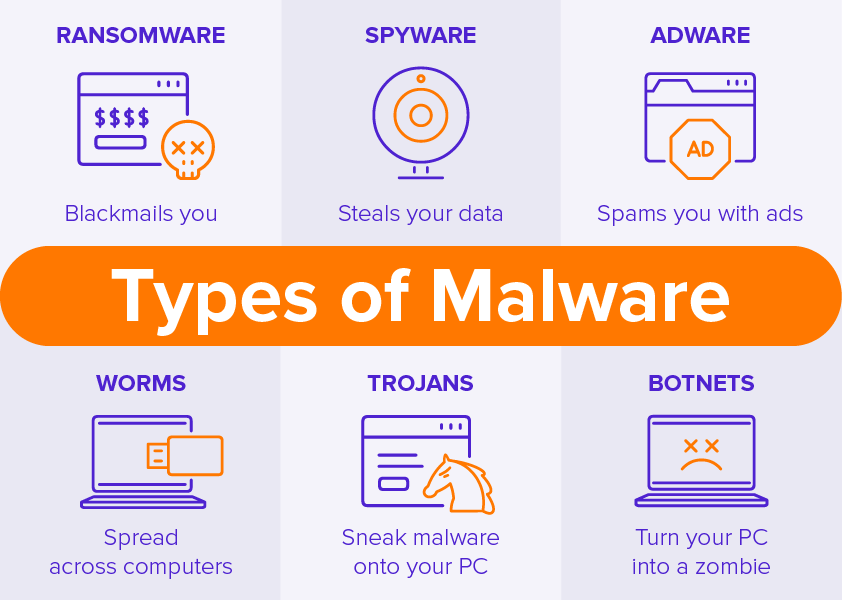
Ransomware
Ransomware is a very common type of malware. Once ransomware infects a user’s device, it encrypts information on the device or locks the user out and demands the owner of the computer to pay a ransom in order to regain access to the device or information on it. Often, payment is requested in the form of cryptocurrency.
Keyloggers
This type of malware records everything a user types on his or her computer and sends the recorded information to the malicious actor who created the program. Keyloggers are often used to get ahold of passwords, logins, credit card details, etc.
Trojan horses
As the name hints, Trojan horses are harmful software programs that are disguised as regular software. In most cases, a Trojan horse malware program remains dormant for a period of time before being activated by the threat actor. Trojan horse malware is typically spread through social engineering tactics.
Computer worms
This type of software is similar to computer viruses, as they can also replicate and spread identical copies of the malicious software to other devices through emails and messaging systems. The main difference between worms and viruses is that the former doesn’t need a host program.
Bots and botnets
Botnet malware infects your computer or any other digital device and allows threat actors remote control over it. The hacker can then send all the devices in his or her control to attack a website, server, application, etc. of their choice.
Logic bombs
Logic bombs are malware programs that remain dormant in your device until a certain moment. This could be a pre-defined activation date or a certain event, like the 100th time your computer is turned on. The biggest danger of logic bombs is that antiviruses can’t detect them until they are activated and at that point, it might be too late.
Rootkits
Rootkits give the malicious actor a huge amount of control over the infected device. Potentially, the threat actor can even gain complete control of the device remotely. This means he or she can view the user’s activity, modify system settings, execute applications, etc.
Spyware and adware
Adware is usually an annoying, yet harmless program that floods your device and browser with ads. Adware is often installed on your computer when you’re downloading an infected file from the internet.
Spyware is much more dangerous, as it allows the threat actor to track all of your activity on the device, collect your passwords, personal information, browsing history, etc.
Frequently asked questions
How do you get malware?
It is estimated that over 90% of malware is delivered by email. This means that hackers use simple spam emails or social engineering techniques to send out emails containing malware attachments or links that automatically download harmful software to the recipient’s computer once they are clicked.
Can you remove malware from a computer?
Yes, luckily, removing most malware from a computer is a fairly standard procedure. You just need to use an effective and reputable malware scanner to detect and remove malware from your device. Keep in mind that if your computer was infected with malware even though you had an anti-virus program installed on it, you need to download a different malware scanner to remove the virus.
What are some signs that my computer is infected with malware?
Computers that are infected with malicious software often start operating slower than before, showing strange messages or performing unauthorized actions, such as sending emails without being prompted by the user, rebooting at random times, etc.