Table of Contents
What is endpoint security?
Endpoint security refers to the security of devices that connect to a network, or network endpoints. These devices include mobile phones, tablets, laptops, and even servers located at data centers. Ultimately, the goal of endpoint security is to minimize the security risk that comes from the devices that connect to your company’s network.

Why is endpoint security so important?
With so many people working remotely during the Covid-19 pandemic, endpoint security is more important than ever. When all employees use only company-owned and managed devices to access corporate networks and resources, it’s easy to ensure security. But with each personal device, the threat level rises significantly. Endpoint security should be used as an addition to centralized security measures.
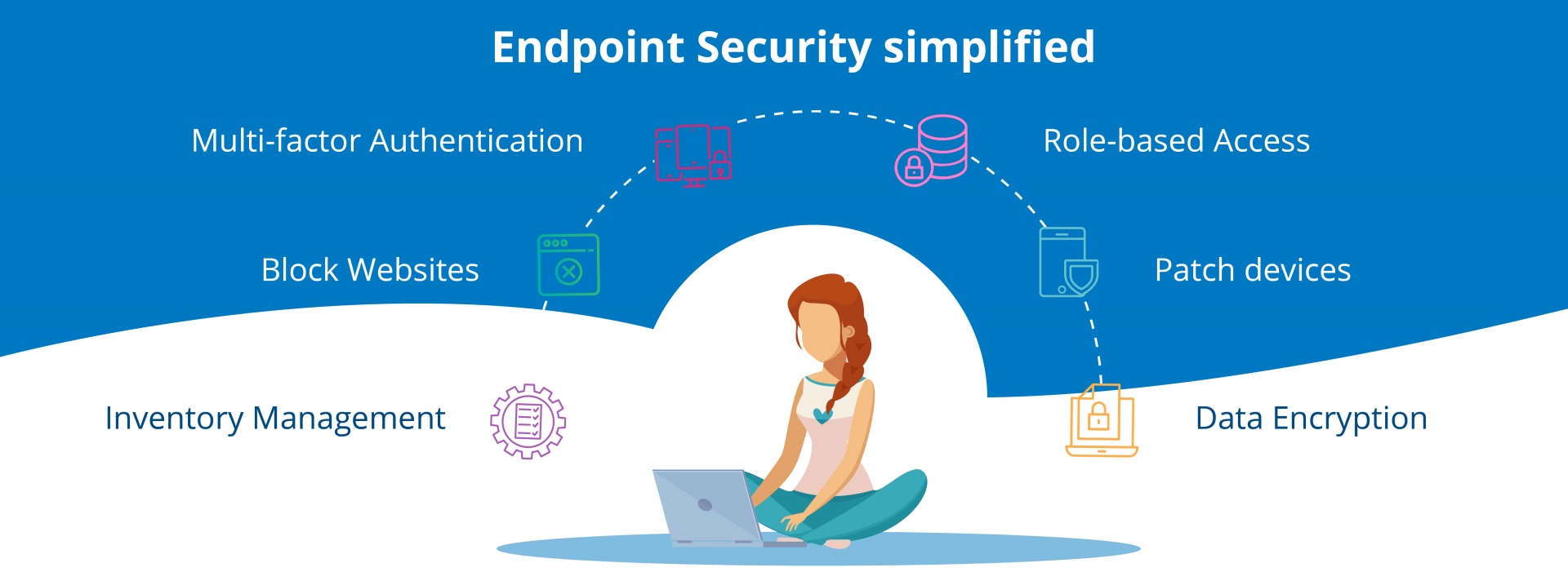
Setting certain endpoint security requirements for devices that are requesting network access will allow businesses to have more control over the numerous new access points and minimize the threat level imposed by these devices. Endpoint security tools will also allow the company to monitor endpoints for any threats that may arise and block those threats before they cause any harm.
How is endpoint security different from anti-virus software?
While certain anti-virus programs could be viewed as very simple endpoint security tools, ultimately, software that guarantees endpoint security is a lot more sophisticated than any anti-virus program. Endpoint security tools typically work to prevent loss of data, protect the network from insider threats, encrypt the device, its disk, and email, control access to the network, and more. In addition to being installed on devices, endpoint protection software should also be placed on the central server in the network.
What are the most important components of endpoint security?
While there are numerous things that go into effective endpoint security, the two most important components are application control and device encryption. If all the information that belongs to your company is encrypted on the employees’ devices, it minimizes the chances of data leaks.
At the same time, application control performed by endpoint security tools stops unauthorized applications from performing any actions on the device. This means that even if an employee downloads a potentially harmful program to his or her computer and installs it, it will not be able to do any harm since it will be blocked by endpoint security software.