It’s not a secret to anyone that WiFi is incredibly convenient in the workplace but at the same time, improperly set up and secured WiFi often results in costly hacker attacks and security breaches. Conducting regular wireless penetration tests can help minimize the risks associated with hacker attacks on WiFi networks and access points. In this article, we will explain what a wireless penetration test is and how it is conducted.

Table of Contents
What is a wireless pen test?
A wireless penetration test is a thorough examination of all the connections between various devices and a business or even home WiFi.
Wireless penetration test stages
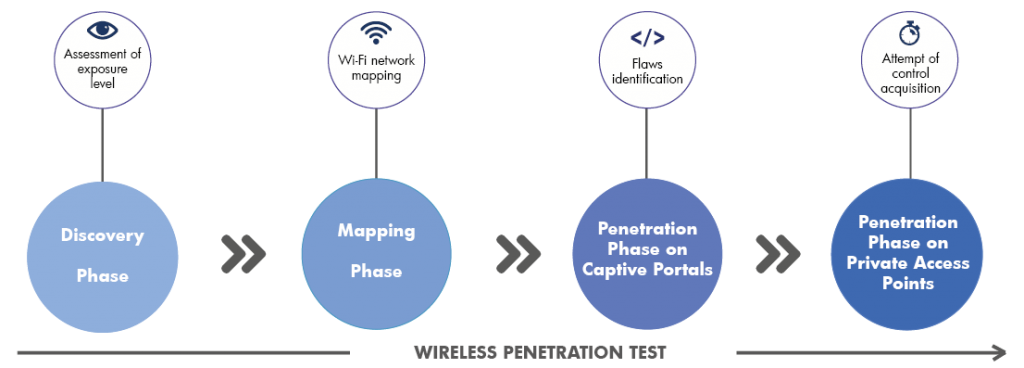
The first stage of a wireless pen test is reconnaissance. During this step, a cybersecurity specialist will use the War Driving technique along with equipment that includes a wireless network adapter, packet capture software, a laptop and a car to drive around the premises of the company and gather information via wireless networks. This information will usually be encrypted.
During the second stage of the test, the specialist will identify wireless networks by setting his or her computer’s wireless card in “monitor” mode and scanning wireless traffic on different channels.
The third stage of the test focuses on identifying vulnerabilities on all the discovered WiFi access points. One of the most common vulnerabilities identified at this stage is a weakness in the four-way handshake process. When a user tries to connect to a WiFi access point, the devices generate and transmit a pre-shared key. As this key is transmitted, a hacker can attempt to extract the password, which will allow him or her to become authenticated with the WiFi access point.
During the following stage, the hacker will try to exploit the identified wireless weaknesses. In the case of a 4-way handshake vulnerability, the hacker will need to first de-authenticate a WiFi user that is already legitimately connected to the WiFi point in question, then capture the 4-way handshake key when the WiFi user attempts to reconnect to the WiFi point and finally run a dictionary attack in an attempt to extract the password from the captured key.
The final steps of a network pen test are reporting and remediation. The cybersecurity specialist or team prepares a report with the results of the penetration test, vulnerabilities that were identified, potential risks and methods used during the test. This report should also include recommendations on how to eliminate the vulnerabilities.

Frequently asked questions
Can you perform a wireless penetration test remotely?
No, in most cases, it is not possible to perform a wireless pen test remotely, as the individual performing the test needs to be close in the range of the WiFi source. Therefore, WiFi penetration tests are usually performed on-site.
What vulnerabilities are typically exposed during a wireless pen test?
The most dangerous vulnerabilities are usually located at the WiFi access point. These often include inadequate NAC (Network Access Controls) and the lack of MAC filtering.
What software is used to perform WiFi penetration tests?
Cybersecurity specialists typically use tools from the Kali Linux OS to conduct wireless penetration tests. The Airplay-NG is the most commonly used tool.