
Two-Factor Authentication
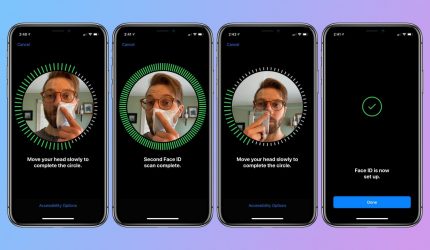
Is it safe to use FaceID or fingerprint to unlock my phone?

Data loss prevention best practices and software

The ultimate guide to vulnerability scanning best practices

How to perform web application penetration testing?
How to use SIEM solutions to protect your company?

SIEM vs IDS – how are they different?
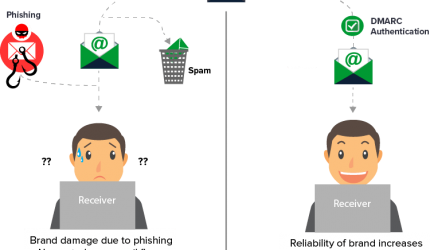
DMARC authentication – is it enough?

How to prepare for penetration testing?

Cybercrime prevention

Social engineering testing

Software penetration testing

Top 3 elicitation techniques in intelligence and social engineering

Cyber insurance cost

Cyber insurance
Cybersecurity intelligence sharing

HIPAA physical safeguards rules

Top 5 industries targeted by cyberattacks
Types of penetration testing for businesses
Access control policy and procedures

Red teaming and penetration testing

Using SMS for two-factor authentication is dangerous

Google Safe Browsing

How to protect your social media account?

How to protect your business from cyber crimes

Fast takedown: How important is fast takedown?

Financial Crimes in Darkweb

Mobile app security: What is it? Advices and tips

Latest phishing attack trends and how to avoid them

What is anti-malware software?

5 tips for better mobile app security

What is cyber-defacement and how to deal with it?

What is a man in the browser attack?

What is scareware?

Mobile app fraud

Why do you need to have a strong password?

What is vishing?

What is a BEC scam and how can you avoid it?

How to stop phishing emails from hurting your business?

Social media security best practices for your small business

Do my employees need cyber security awareness training?

What is phishing?

The future of IT and its impact on your business

How to protect your small business from cyber attacks today

How to secure WiFi Network in Small Business

How to protect your Brand from informational breaches

Tips on How To Train Your People Cyber Security
HackControl does not only provide cybersecurity and brand protection services to companies and organizations. We also work hard to educate our clients and the general public on the importance of cybersecurity, various cybersecurity threats that exist today and action your business or you personally can take to minimize those threats. In our cybersecurity blog, you will find hundreds of useful and easy to understand articles about phishing, social engineering, different types of hacker attacks, penetration tests, cyber insurance and more. We add new articles to our blog almost every week, so even if you can’t find the information you’re looking for now, remember to check in later to see if we cover your topic in the future or contact our specialists for a consultation.